TACKLE SECURITY THREATS HEAD-ON WITH CYBER6.
Fortify your endpoints with advanced monitoring and threat detection for unparalleled peace of mind.

Focus on your business with compliance-ready security solutions tailored to your unique needs.

Stay ahead of evolving threats with our continuous improvement approach that ensures robust protection.
Evidence Unveiled
Forensic Analysis: Unravel the complexities of digital evidence with our expert analysis, ensuring every detail is uncovered across Windows, Linux, Android, and iOS platforms. Incident Response: Swiftly respond to security breaches with our comprehensive incident response services, minimizing damage and downtime on any device or operating system. Digital Forensics: Leverage our cutting-edge tools and techniques to extract, analyze, and preserve digital evidence, ensuring its integrity and admissibility regardless of the source.






Elevate Your Cybersecurity Posture
At Cyber6ix, we empower clients to understand their true security posture. Our advanced analytics platform provides real-time visibility into compliance and security scores, enabling proactive remediation and benchmark tracking. Partner with us to confidently navigate the evolving threat landscape, making informed decisions to protect your organization's digital assets and reputation.
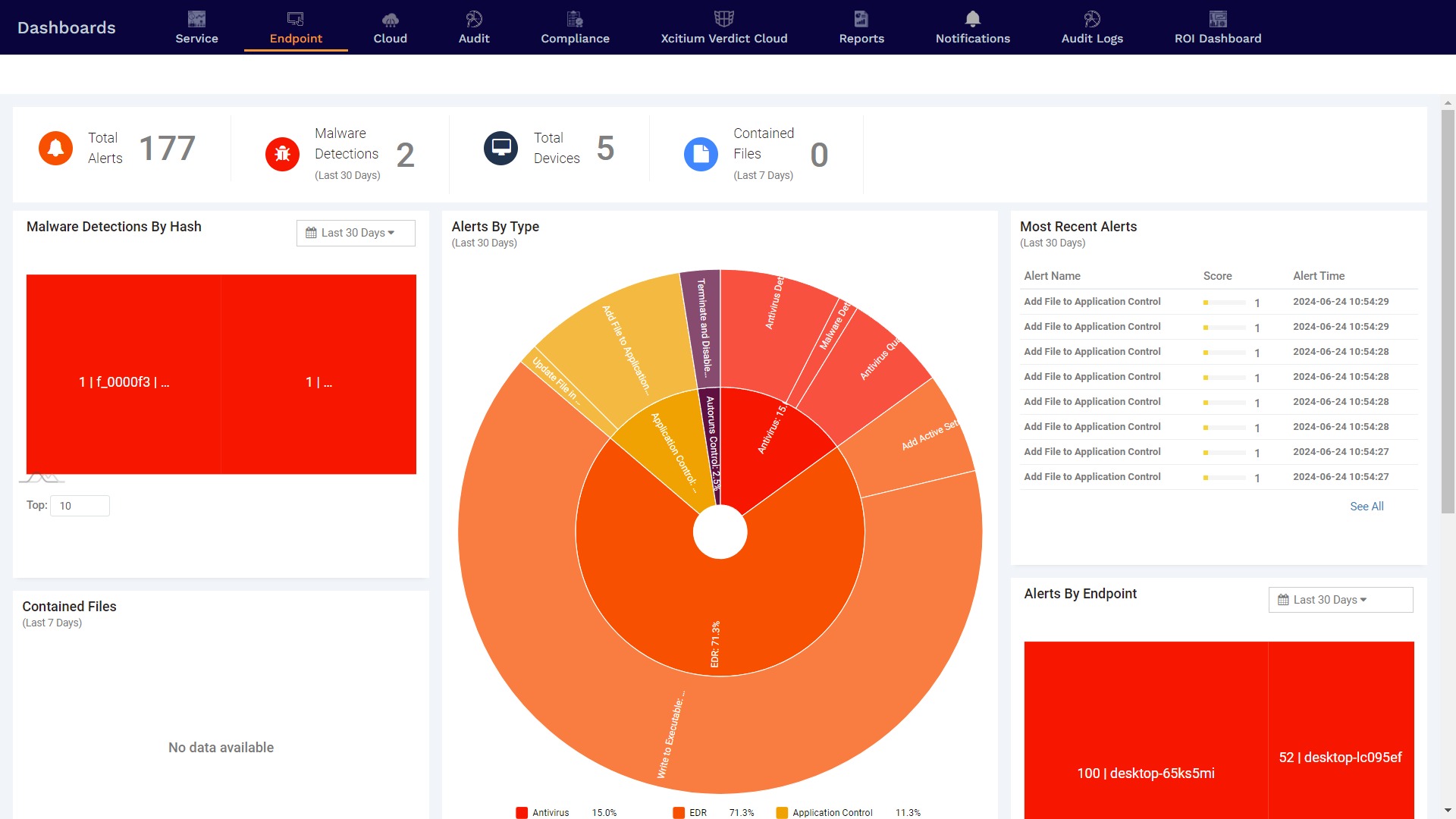
Real-Time Network Health Overview
Our system provides a comprehensive view of your network's health and performance. The dashboard features key metrics such as Compliance Level, depicted with a multi-colored pyramid indicating adherence to standards, and Tasks Completion, shown through a circular progress indicator. Additionally, the Test Results section visualizes performance data over time, with an option to view past results for historical comparison. This interface ensures that you can quickly assess compliance, monitor task progress, and analyze performance trends, enabling proactive management and robust endpoint security.